Security testing is the analysis of software vulnerability to all kinds of attacks.
The task of this testing is to determine the weaknesses of the system, which can lead to illegal intrusion and cause not only the loss of important information but also harm the reputation of the product makers.
In security testing, QA engineers check the way how built-in security tools respond to penetration.
During the test, the specialist performs the role of the cracker by reproducing his possible actions:
- Password cracking;
- System suppression;
- Introduction bugs as a way to penetrate during system recovery;
- Analysis of available data is a way to find a way to penetrate the system;
- An attack on the system.
If we talk about security testing services, we should analyze the SQL Injection method.
SQL Injection is a vulnerability by which a hacker edits or creates current SQL queries to expose hidden data, replace it, or execute dangerous operating system commands on the server side. The attack is based on a program that builds SQL queries from data entered by the user and static parameters.
The causes of the vulnerability are the insufficient level of protection of access to databases, input parameters, no control measures, use of irrelevant technologies, and vulnerable code.
SQL Injection vulnerability occurs when a developer creates a dynamic query on a database that includes user data. Today, it is very difficult to refuse such queries, so SQL Injection will be dangerous soon.
A common tool for penetration testing is sqlmap. It includes a high-quality detection mechanism that is used in this tool which has a large amount of functionality for the tester, as well as a wide range of options. It is also a tool for automating SQL implementation.
This penetration testing tool is quite popular due to some advantages, such as providing support, by connecting directly without SQL injection. Also, it’s support for loading a variety of database files that underlie the file system if the database software is MySQL, PostgreSQL, MySQL, Microsoft SQL Server, etc.
The features of sqlmap are quite extensive, from the ability to read and write files on a remote file system to a variety of hacking capabilities. Using this tool to test database servers can help secure your product by eliminating the possibility of hacking by identifying vulnerabilities.
Testing of a hack with the sqlmap tool is done by running a command from a terminal, using the Python interpreter (since sqlmap is written in Python, it needs to be installed).
Sqlmap contains different parameters for finding vulnerabilities, which can be examined using the following commands as an example:
sqlmap.py -h
sqlmap.py –hh
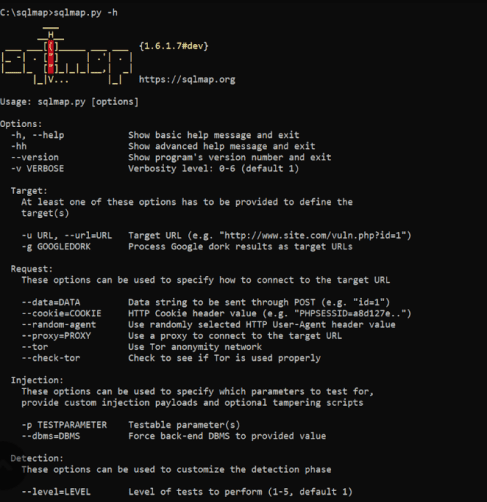
Using “sqlmap.py -h” – example from the Internet
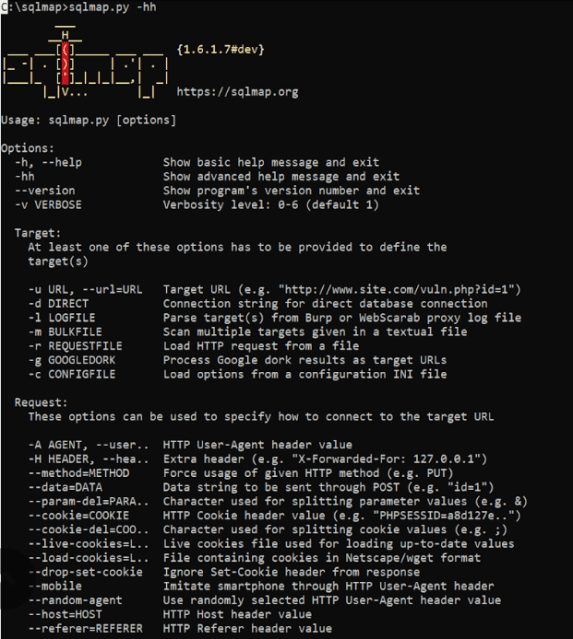
Using “sqlmap.py -hh” – example from the Internet
Sqlmap functions using GET by default. But it is also possible to specify POST parameters. And host testing is provided by the command below.
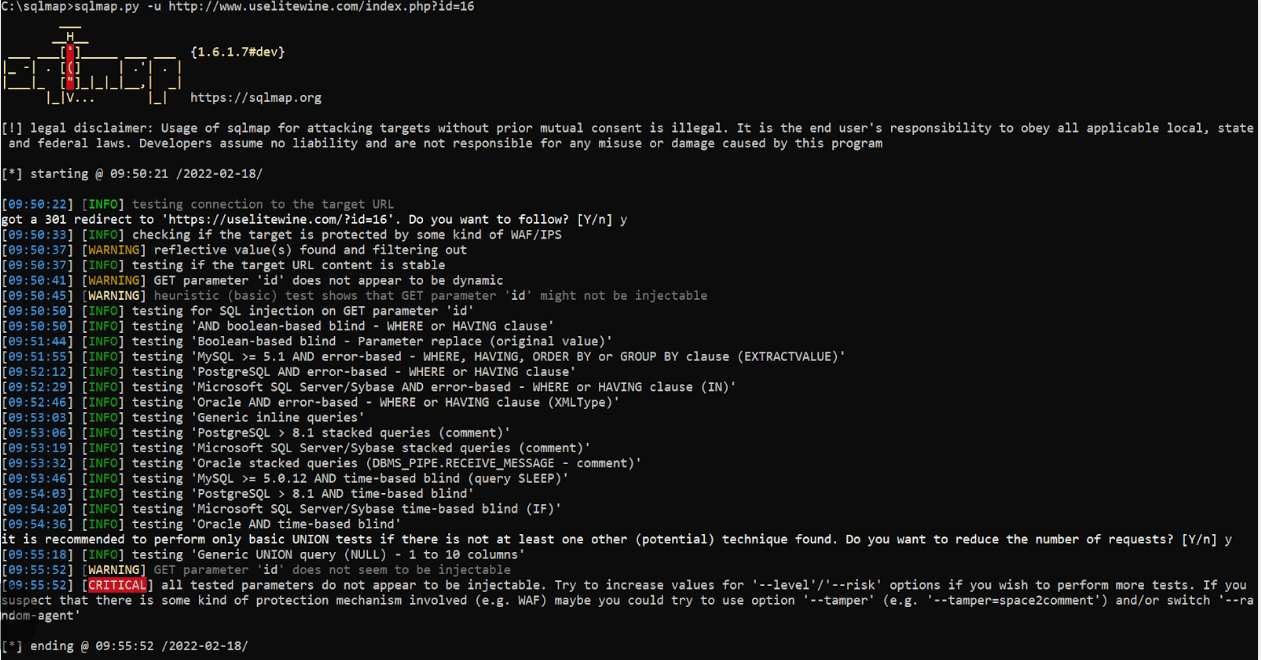
Testing the host – example from the Internet
Short Conclusion
With sqlmap, you can quickly test for system weaknesses. This, in turn, will allow securing the product and avoiding unforeseen negative events, which may occur after the software is officially released.









Leave A Comment